- The main threats combine advanced malware, social engineering, and misconfigurations exploited by increasingly automated attackers.
- The impact ranges from economic losses and operational shutdowns to legal sanctions, reputational damage, and intellectual property theft.
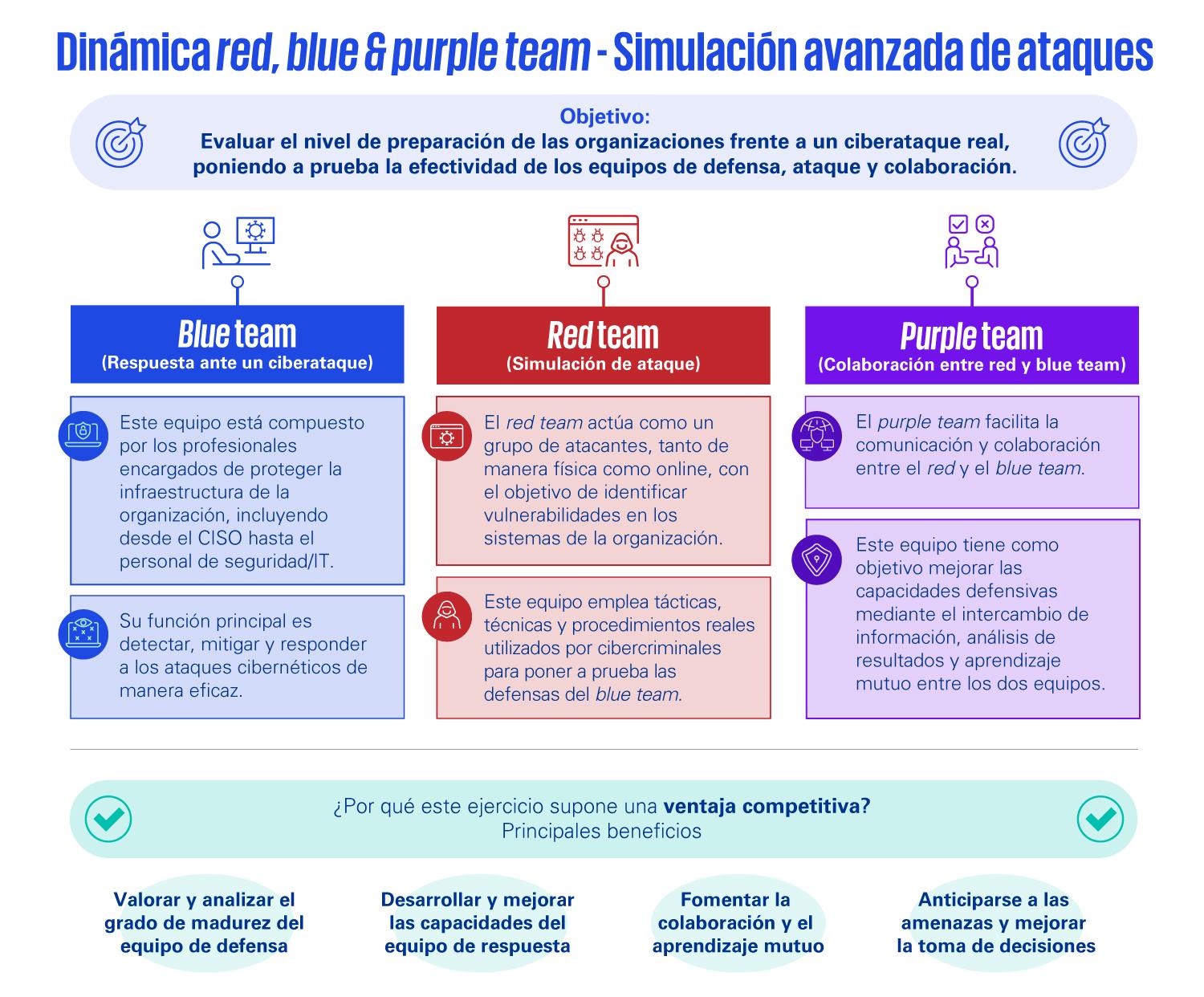
- Effective defense requires layers of technical protection, good cyber hygiene, continuous monitoring, and a robust incident response plan.
- Continuous training and the integration of AI in cybersecurity are key to bridging the talent gap and anticipating new attack tactics.
La Cybersecurity has become a daily concern for any IT professional. Cloud securityRemote work, corporate mobile phones, and artificial intelligence have dramatically increased the attack surface, and cybercriminals are wasting no time: they automate attacks, refine social engineering techniques, and exploit any misconfiguration or human oversight to infiltrate organizations.
For technical teams, it is no longer enough to "install an antivirus and a robust firewall". Gain a thorough understanding of the main cybersecurity threats for IT professionalsUnderstanding the real impact of cyber threats on business and the best practices for mitigating them is key to maintaining operational continuity, avoiding legal penalties, and protecting critical data. Throughout this article, you will see, in detail and with a very practical approach, which risks are dominating the current landscape and what you can do to make it much more difficult for attackers.
What is considered a cybersecurity threat today
When we talk about cybersecurity threats, we are referring to any event, weakness, or malicious activity that could compromise the confidentiality, integrity, or availability of systems and data. This includes everything from "classic" malware (viruses, worms, Trojans, ransomware, spyware) to unpatched vulnerabilities, poor user practices, cloud misconfigurations, or state-sponsored targeted attacks.
These threats take advantage technical gaps and human errorsOutdated software, weak passwords, excessive permissions, phishing emails that trick employees, poorly secured cloud storage, third parties with weak security, etc. The result can range from a one-off data breach to a complete company shutdown for days.
In parallel, the incorporation of artificial intelligence and automation to cyberattacks It allows for simultaneous campaigns against thousands of companies, the generation of highly convincing deepfakes, and the creation of polymorphic malware that constantly changes its code to evade traditional defensive tools. The challenge for IT professionals is therefore twofold: protecting increasingly complex infrastructures and doing so against faster and more sophisticated attackers.
Real impact of cybersecurity threats on organizations
The consequences of a security incident go far beyond the initial scare. Each breach can trigger a cascade of impacts on different fronts: economic, reputational, legal, and operational. Understanding this dimension helps justify investments and prioritize security projects for management.
In financial terms, The direct and indirect losses can be enormousIn addition to fraudulent transfers, ransomware ransom payments, and financial data theft, there are costs associated with downtime, overtime for the response team, external forensic services, notifying affected parties, and campaigns to restore trust. Many studies place the average cost of a breach in the tens of thousands of euros for SMEs and in the millions for large corporations.
Reputational damage is equally or even more serious: When a customer sees their information exposed, they immediately lose trust.This loss of credibility translates into canceled contracts, decreased sales, and difficulties in closing deals with new partners or accessing certain public tenders. Returning to the previous level of trust could take years, if it is ever achieved at all.
On an operational level, an attack can completely paralyze critical processesBilling systems down, production plants shut down, online services out of service, supply chains disrupted… Any IT professional who has experienced a massive ransomware attack knows that the pressure on the business is brutal when you can't sell, produce or serve customers.
Finally, we must not forget the legal and regulatory consequencesRegulations such as the GDPR in Europe and other sector-specific laws require adequate protection of personal data and notification of breaches within very specific timeframes. A failure can result in significant financial penalties and litigation with clients, suppliers, or even employees. At the same time, the theft of intellectual property (blueprints, algorithms, formulas, source code) can squander years of R&D investment and hand a competitive advantage to rivals.
Main types of technical threats to IT professionals
From a purely technical point of view, companies face a wide range of risks that impact infrastructure, applications, and users. Knowing the most common types of attacks This is the first step in defining appropriate security controls and architectures.
Malware in all its variants
Malware remains one of attackers' favorite weapons. Under this umbrella we find malicious software designed to infiltrate, damage, or control systems without the knowledge of the user or administrator. Its most frequent forms include:
- Ransomware: It encrypts files and systems with keys that only the attacker controls, and demands payment (usually in cryptocurrency) to restore access. The most advanced groups combine encryption with data theft, threatening to publish the information if payment is not made, even if backups exist.
- Trojan Horses: They present themselves as legitimate programs (free software, supposed cracks, "miracle" utilities) but, when executed, they deploy hidden malicious functionality that can range from opening backdoors to downloading more malware.
- RAT (Remote Access Trojan): Trojans specifically designed to give the attacker complete remote control of the machine. They allow spying and the extraction of sensitive information., install new components or pivot to other internal systems.
- Spyware: code designed to record user activity, capture credentials, bank details, browsing habits, or valuable business information, which is then sent to servers controlled by the attacker.
- Cryptojacking: Malware that hijacks the computing power of servers, workstations, or even IoT devices to mine cryptocurrencies without the owner's knowledge, degrading performance and increasing energy costs.
Technology fails, but so do people. Social engineering exploits. psychological weaknesses and user habits to get them to do exactly what the attacker needs: click a link, disable protection, hand over credentials or sensitive data.
Within these tactics, the Phishing remains the starEmails are sent that mimic communications from banks, suppliers, government agencies, or even the company itself, to lure users to fake websites or force them to download malicious attachments. In its most targeted form, spear phishing focuses on specific profiles (finance, executives, IT administrators) using public or internal data to lend credibility to the deception.
The same concept applies to other channels: smishing when the lure arrives via SMS to mobile, taking advantage of the fact that in these messages it is more difficult to verify the URL; and vishing when the attack is carried out by phone, impersonating a technical support, the bank or a provider that requires "verification" of information.
With the emergence of generative artificial intelligence, the following have gained strength: voice and video deepfakesThese tools can impersonate managers or department heads to order urgent transfers or share confidential information. They reduce the cost and simplify campaigns that previously required much more manual effort.
Attacks on web applications and APIs
Web applications and APIs are, for many companies, the most exposed part of its attack surfaceA failure in input data management, access controls, or parameter validation can open the door to very damaging attacks:
- SQL Injection (SQLi): Manipulating database queries by injecting malicious code into input fields. If the application does not properly clean up this data, the attacker can read, modify, or delete information, and even take control of the database server.
- Remote Code Execution (RCE): Vulnerabilities that allow an attacker to execute commands on the server where the application runs, usually by exploiting buffer overflows or other logical errors. This type of failure is usually critical because it translates into almost total control of the affected system.
- XSS (Cross-Site Scripting): Injecting malicious scripts into pages that are then presented to other users. These scripts can steal session cookies, modify browser content, or redirect to fraudulent pages without the user's knowledge.
Supply chain attacks
It is increasingly common for attacks to target not the company itself, but its partners. Supply chain attacks exploit relationships of trust with software providers, integrators, cloud services or consultancies.
A classic scenario is that of a service provider with remote access To internal systems: if the attacker compromises your network, they can use those legitimate credentials to gain access to the client organization with very little suspicion. Another vector is the manipulation of third-party software or updates: injecting malicious code into update packages that the client installs, trusting their source completely.
Furthermore, almost all modern applications integrate open source libraries or third-party modulesA serious vulnerability like Log4j demonstrated the extent to which a seemingly small component can pose an enormous risk on a global scale when widely distributed. For IT teams, inventorying and managing the risk of external components is now unavoidable.
Denial of Service (DoS and DDoS) attacks
Attacks against availability are aimed at to take services and applications out of the game so that legitimate users cannot access it. In its distributed (DDoS) form, thousands of compromised devices bombard the victim's systems with traffic, saturating bandwidth, CPU, or application resources.
Some groups use denial of service as extortion tool (RDoS)They threaten massive attacks if a ransom isn't paid, or combine them with ransomware campaigns to increase pressure. In other cases, DoS attacks are executed by exploiting specific vulnerabilities that cause crashes or excessive resource consumption when they receive malformed inputs.
Man-in-the-Middle attacks (MitM and MitB)
In Man-in-the-Middle attacks, the target is intercept and, if possible, modify the traffic between two parties who believe they are communicating directly and securely. If the communications are not properly encrypted, an attacker can read credentials, banking details, or business information in plain text.
One particularly dangerous variant is the Man-in-the-Browser (MitB)This attack involves the attacker compromising the user's browser through malicious plugins or malware, and manipulating data just before it is displayed or sent to the server. This allows them to alter transfer amounts, modify forms, or capture all input without raising any visible suspicion.
Advanced threats and key trends for IT professionals
In addition to the classic "backup" of attacks, the current landscape brings Very clear trends that IT teams cannot ignore: increased role of AI in cybercrime, DNS risks, cloud misconfigurations, insider threats, and state-sponsored operations.
Threats based on artificial intelligence
Artificial intelligence is not exclusive to defenders. Increasingly, Cybercriminals rely on AI and machine learning to scale, fine-tune, and customize your attacks. Some examples:
- Mass generation of phishing emails and messages with natural and error-free texts, adapted to the language and context of the victim.
- Automation of the search and exploitation of vulnerabilities in exposed systems, prioritizing targets with a higher probability of success.
- Malware development capable of learning from the environment and modifying its behavior to evade detections based on signatures and static patterns.
- Creation of voice and video deepfakes to reinforce social engineering campaigns targeting high-value profiles.
In parallel, companies begin to strategically integrate GenAI into your defenses to accelerate research, improve anomaly detection, and address the cybersecurity talent gap, which many officials recognize as one of today's biggest challenges.
DNS tunnels and abuse of the domain name system
DNS is a fundamental part of the Internet and, for that very reason, an ideal channel for hiding malicious trafficDNS tunneling consists of encapsulating data within seemingly normal DNS queries and responses, thus bypassing many perimeter controls that only look "over the surface" at this traffic.
This technique allows you to extract sensitive information drop by drop. or maintain command and control channels with internal malware without raising suspicion. Detecting this type of activity requires monitoring for anomalous patterns in queries, sizes, unusual domains, or strange statistical behavior in DNS traffic.
Configuration errors and poor cyber hygiene
A large number of incidents originate in incorrect settings and unsafe habitsCommon examples:
- Overly permissive firewalls or cloud security groups, with ports open to the world that shouldn't be.
- Data stores in cloud services configured as “public” by mistake, exposing sensitive information without any authentication.
- Use of default credentials or weak and reused passwords across multiple services.
- Failure to apply security patches and firmware updates, leaving known vulnerabilities open for months.
- Lack of reliable, up-to-date, and tested backups, which prevents a quick recovery from a ransomware attack.
All of this falls under what we might call poor cyber hygieneFailing to follow basic best practices undermines any other security effort. Automating configuration audits, applying principles of least privilege, and training users are critical tasks for closing these obvious vulnerabilities.
Internal threats and human error
People with legitimate access to systems and data pose a risk that is often underestimated. Insider threats can be malicious or accidental.:
- Disgruntled employees who steal information to sell it, leak it, or take it to the competition.
- Contractors or partners with more privileges than necessary who decide to abuse them.
- Team members who, without malicious intent, share data through insecure channels, send emails to incorrect recipients, or upload sensitive files to personal cloud services.
Mitigating this risk involves granular access controls, periodic review of permitsMonitoring for suspicious activity (UEBA, DLP) and a strong security culture within the organization are essential. When someone leaves the company, the immediate revocation of credentials and access must be an automatic and non-negotiable process.
State-sponsored attacks and forward operations
At the other end of the spectrum, we find operations carried out or supported by nation-states. These Attacks are usually motivated by political, military, or economic factors. and they focus on critical infrastructure, public administrations, strategic companies (energy, health, finance) and key technology providers.
Its level of sophistication is high: exploitation of 0-day vulnerabilitiesComplex infection chains, months of silent surveillance before action, customized tools, and large-scale coordinated campaigns. Although many SMEs are not a direct target, they can be affected as weak links in the supply chain of high-profile organizations.
Prevention and defense strategies for IT teams
Given such a complex scenario, the only reasonable way out is adopt a proactive, comprehensive, and layered approachThere is no silver bullet, but there is a set of practices and technologies that, combined, drastically increase the cost of attack for the adversary.
Patch and Update Management
The first line of defense goes through keep systems, applications, and devices up to dateEstablishing regular update windows, using inventory and automatic patching tools, and prioritizing critical vulnerabilities reduces the known attack surface.
It's not just about operating systems: firmware for routers, switches, firewalls, endpoints, hypervisors, third-party applications And open-source components must be included in the update radar. Ignoring this is like handing attackers a catalog of already documented exploits.
Robust authentication and access control
Minimizing the impact of stolen credentials requires implement multi-factor authentication (MFA) Where possible, this should be accompanied by strong password policies and regular password rotation. In complex corporate environments, adopting Zero Trust models helps to avoid trusting any device or user by default, even if they are "inside" the network.
Apply the principle of least privilege (giving only the permissions strictly necessary for each role) greatly limits what an attacker can do even if they manage to access a legitimate user's account.
Continuing education and safety culture
As all reports show, the human factor remains one of the weakest links. That's why, Cybersecurity training cannot be a one-off course It's something that's done once and forgotten. It needs to become a continuous program, updated and adapted to different profiles within the company.
The contents should cover from basic awareness (recognizing phishing) (from recognizing phishing, protecting devices, and safe behavior on social media and cloud services) to regulations, area-specific best practices, and advanced specialization for technical profiles. A learning-by-doing approach, with realistic attack simulations, hands-on labs, and live sessions with experts, is usually the most effective way to solidify knowledge.
Network, endpoint, and data protection
On the technological side, it is essential to combine different controls: next-generation firewalls, intrusion detection and prevention systems (IDS/IPS)Content filtering, network segmentation, advanced endpoint solutions (EDR/XDR), data encryption in transit and at rest, and DLP tools to prevent unauthorized exfiltration.
Backups play a critical role: frequent backups, logically disconnected from the main network and are tested periodically to ensure that the restoration works, making all the difference in a ransomware incident or mass data wipe.
Incident response plans and threat intelligence
No environment is 100% safe, so it's vital to assume that, sooner or later, there will be incidents. Have a well-defined incident response planTested through simulations and known to all involved, it drastically reduces chaos when the moment of truth arrives.
Additionally, rely on real-time threat intelligenceWhether proprietary or from specialized providers, it allows you to adjust detection rules, block known malicious infrastructures and anticipate new campaigns before they hit the organization hard.
In this context, next-generation cybersecurity solutions capable of detect anomalous behavior, automate responses (Isolating teams, killing malicious processes, reverting changes) and correlating events in endpoints, network and cloud are great allies for security teams that, in many cases, are overwhelmed.
For IT professionals, the challenge is no longer just patching things up and putting out fires, but lead a coherent security strategy that integrates technology, processes, and people. Threats will continue to evolve, AI will continue to play both sides, and the cybersecurity talent gap won't close overnight. That's precisely why organizations that invest early in a robust security culture, intelligent automation, and continuous training will be best positioned to withstand the inevitable challenges that will inevitably arise.
